Cyber Resiliency in Government: Key Actionable Insights from the 2022 Microsoft Digital Defense Report
Worldwide Public Sector Security Lead Alvaro Vitta breaks down the 2022 Microsoft Digital Defense Report as it relates to cyber resiliency and outlines actions that governments must take now on to protect their digital ecosystems.
As geopolitical forces and cybercriminal activity continue to shape the cybersecurity landscape and its ever-growing scale and complexity – government organizations find themselves in a complex cyber race to adapt and respond to threats to continue to provide critical services for the wellbeing and safety of their citizens.
The release of Microsoft’s 2022 Digital Defense Report dives into this issue – the evolving digital threat landscape. The report shares unique insights and outlines crucial actions that can be taken right now to protect your organization.
I had the pleasure of recently speaking with Tom Burt, the author of the Microsoft 2022 Digital Defense Report and Microsoft’s Corporate Vice President of Customer Security and Trust, for the Government Cyber Resiliency Episode in the Public Sector Future podcast. We spoke about the evolving digital landscape and the need for cyber resiliency – the ability for governments to prepare for, respond to and recover from cyberattacks and security breaches.
From our conversation and the insights from the Microsoft 2022 Digital Defense Report, it is very clear that to minimize the risks associated with cybersecurity disruptions to government operations, Government organizations must have a solid cyber resiliency foundation.
There are four core pillars that a Government organization must focus on as part of establishing a solid cyber resiliency foundation that enables their employees to leverage the digital infrastructure necessary to provide critical citizen services. Let’s take a look at these four core pillars:
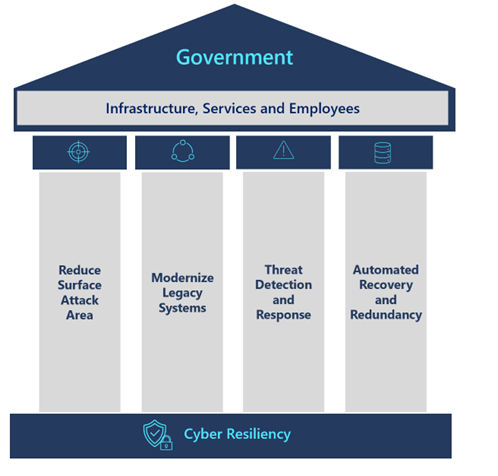
1. Reduce Surface Attack Area
An effective cyber resiliency government program starts with identification of the most critical on-premises and online services, business processes, dependencies, personnel, vendors, and suppliers.
The successful human-operated ransomware infection of an entire organization relies on access to a highly privileged account like a domain administrator, or abilities to edit a group policy.
75% of human-operated ransomware attacks use acquired elevated compromised user account to spread malicious payloads.
As these critical high-impact resources are identified, a risk-based prioritization method should be used that considers the risk-level to the organization, cost and effort to implement and remediation impact to end users. High-risk, low effort and low impact areas to implement should be at the top of the remediation list. Parallel efforts should continuously detect and monitor threats, disruptions, potential attack vectors, and system and process vulnerabilities.
Actionable Insights
- Build and manage technology systems that limit the impact of a breach and enable them to continue to operate securely and effectively, even if a breach is successful.
- Focus on common critical assets, support for agility, and architect for adaptability (for example, hybrid and multi-cloud, multi-platform), reduce attack surfaces (for example, remove unused applications and over-provisioned access rights), assume compromised resources, and expect adversaries to evolve.
2. Modernize Legacy Systems
Legacy systems—those developed before modern connectivity tools such as smartphones, tablets, and cloud services became the norm represent a risk to an organization still using them.
Over 80% of security incidents can be traced to a few missing elements that could be addressed through modern security approaches.
Actionable Insights
- Given the native built-in security capabilities in cloud service providers, Government organizations should plan and implement a strategy that modernizes their legacy security systems by moving to hyperscale, AI-Based cloud security solutions.
As part of their security modernization strategy, there are clear areas which organizations can start to address to modernize their approach and protect from threats:
- Identify your critical business data and where it is located. Review information lifecycle processes and enforce data protection while ensuring business continuity.
- Modernize security operations tools by incorporating extended detection and response (XDR) that can provide deep security insights across the digital landscape.
- Secure and limit administrative access to make the environment more resilient and limit the scope of an attack. Employ controls such as just in time and just enough administration.
- Implement access restrictions by enforcing segregation of privileges, least privilege access and utilizing privileged access workstations (PAW) for managing identity systems.
- Multi-factor authentication (MFA) is a critical and fundamental user access control that all organizations should enable. Coupled with conditional access, MFA can be invaluable in fighting cyber threats.
- Follow security configuration baselines and best practices when deploying and maintaining identity systems such as AD and Azure AD infrastructure.
3. Threat Detection and Response
Adversaries are using AI-driven tools and leveraging ‘ransomware-as-a-service’ frameworks which dramatically increase the speed and scale at which they can overwhelm an organization’s defenses. Organizations using humans, legacy security systems and manual processes are particularly vulnerable to these attacks.
The Microsoft Digital Defense Report 2022 shows that 60% of organizations that suffered a ransomware attack, had not invested in security information and event management (SIEM) technology leading to monitoring silos, limited ability to detect end-to-end threats and inefficient security operations. Automation remains a key gap in SOC (Security Operations Center) tooling and processes, forcing SOC staff to spend countless hours making sense of security telemetry.
A comprehensive threat detection strategy requires investments in extended detection and response (XDR) and modern cloud native tools employing machine learning to separate noise from signals and be able to scale up defensive capabilities to match adversaries’ capabilities.
Actionable Insights
- Design and deploy real-time cloud-native, hyperscale response capabilities that enable proactive detection of threats and vulnerabilities.
- Implement threat protection solutions that can protect against known attacks and provide preventive activity against new and anticipated attack vectors, including the ability to automatically remediate.
- Implement extended detection and response anti-malware software to detect and automatically block attacks and provide insights to the security operations. Monitoring insights from threat detection systems is essential to being able to respond to threats in a timely fashion.
4. Automated Recovery and Redundancy
Despite a strong cyber resilience foundation built into an organization’s security program, any organization can be compromised. Therefore, redundancy and recovery plans have to be built into the cyber resiliency program to minimize downtime, ensure operational continuity and safely return to normal healthy operations.
Data from Microsoft’s Security Teams recovery projects shows organizations which suffered ransomware attacks had significant gaps in their security operations including lack of recovery plans. 44% of organizations did not have immutable backups for the impacted systems. Data also shows administrators did not have backups and recovery plans for critical assets such as active directory.
“Before the invasion of Ukraine, governments thought that data needed to stay inside a country in order to be secure. After the invasion, migrating data to the cloud and moving outside territorial borders is now a part of resiliency planning and good governance.”
Cristin Flynn Goodwin, Associate General Counsel, Customer Security & Trust, Microsoft
Actionable Insights
- Document and validate end-to-end recovery and remediation activities related to ransomware attacks against critical services.
- Involve stakeholders in updating your Enterprise Crisis Management Playbooks to include ransomware specific activities and a decision process and guidance to determine if/when to pay for ransomware.
- Ensure a standard exists for creation and validation of backups for critical systems.
- Create playbooks and schedule regular exercises of backup and recovery are done to ensure data can be recovered in the event of a ransomware attack.
- Reduce impact of attacks and disasters through fault isolation and segmentation not only for critical workloads and foundational systems but also by diversifying on-premises data centers across geo-distributed cloud regions.
Conclusion
The scale, complexity and shifting nature of cyberattacks necessitates a strong foundational cyber resilience program. Listen to the Cyber resiliency in Government podcast as I speak with Tom Burt, the author of the Microsoft 2022 Digital Defense Report and we discuss lessons learned, trends, additional insights, examples of Governments doing it right and practical guidance on areas to focus on to strengthen cyber resiliency in a Government organization.
As Government organizations continue to implement the four core actionable pillars, it’s clear that using legacy systems, manual processes, and traditional security operations, will not be sufficient to deal with today’s sophisticated, well-funded and modern cybercriminal organizations or well-structured state-sponsored cyber offensive capabilities.
To match the scale, sophistication, structure and persistence of cyber attackers, Government Organizations must modernize their approach and cybersecurity systems by leveraging the hyperscale and AI-driven automation of cloud-native security platforms to effectively detect, respond and recover from volume of cyberattacks generated by these sophisticated adversaries.
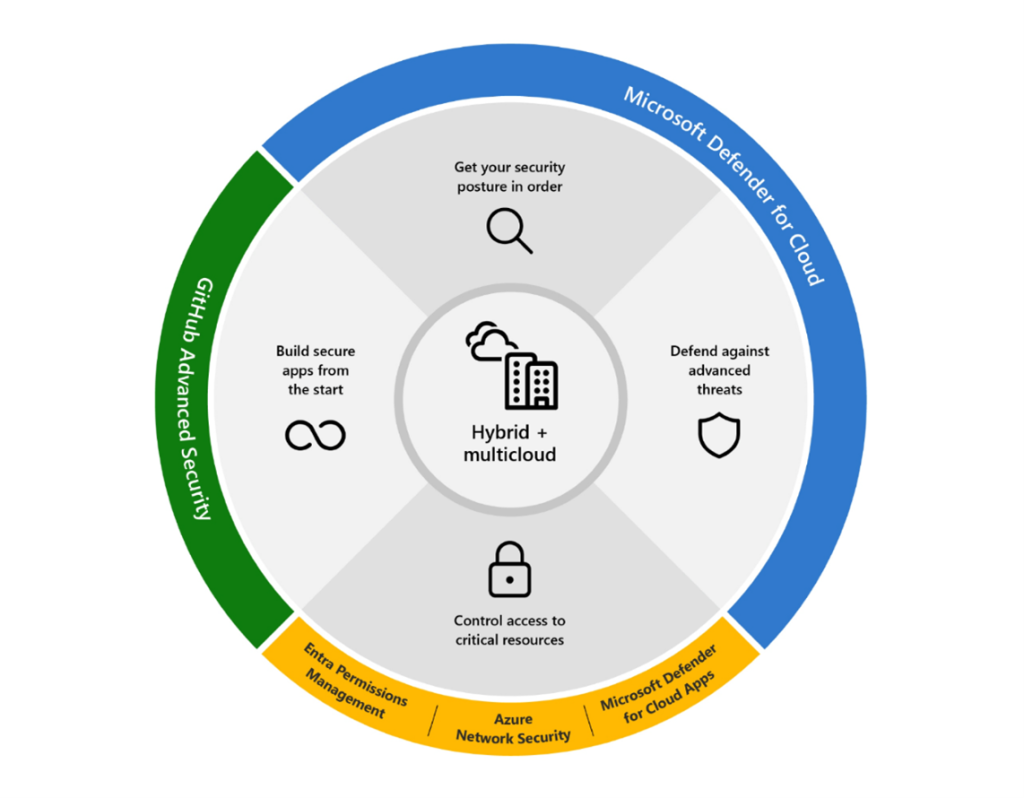
The Microsoft Cloud Security Platform provides Government Organizations with a highly scalable, AI-powered, end to end cloud security platform that strengthens an organizations’ security posture and protect hybrid and multi-cloud workloads with a unified platform, deep signal intelligence, and streamlined administration.
Read the 2022 Microsoft Digital Defense Report
Do your part. #BeCyberSmart
#CyberSecurityAwarenessMonth
#microsoftsecurity
To find out more:
Episode 38: Cybersecurity, Compliance and Cloud: Lessons from Singapore
Episode 37: Military Lessons on Cyberdefense
Find guidance and insights on nation state attacks
Learn more about Microsoft’s secure identity and access solutions
Find out more about Microsoft’s cyber security skilling program
About the Center of Expertise
Microsoft’s Public Sector Center of Expertise brings together thought leadership and research relating to digital transformation in the public sector. The Center of Expertise highlights the efforts and success stories of public servants around the globe, while fostering a community of decision makers with a variety of resources from podcasts and webinars to white papers and new research. Join us as we discover and share the learnings and achievements of public sector communities.
Questions or suggestions?